Recruitment Solutions: Advantages
FIND AND KEEP
TOP TALENT TO
ACCELERATE
YOUR SUCCESS

Be Strategic.
Learn the advantages and benefits of working with our team. We take on the heavy lifting and tactical pieces of recruiting, giving you the freedom to be strategic.
Optimize your recruiting advantage

RPO Programs:
Get end-to-end recruitment support, a dedicated team, full-scale services from candidate generation to onboarding and full RPO services.

Project Recruiting:
Tap into a flexible solution for expanding your capabilities, ideal for hiring ramp-ups, seasonal hiring or new locations.

Strategic Search:
From one person to dozens, we’ll find the top candidates, fully vetted and matched by skill, with the right cultural fit.

Hourly/Contract Recruiting:
Supplement your existing recruiting or sourcing efforts on an hourly basis with our flexible contract recruiting hiring solutions.
Partner with an industry leader



Engage2Excel Recruitment Solutions is a leader in quality, innovation and customer service - recognized by today's most respected analyst groups and professional HR associations.
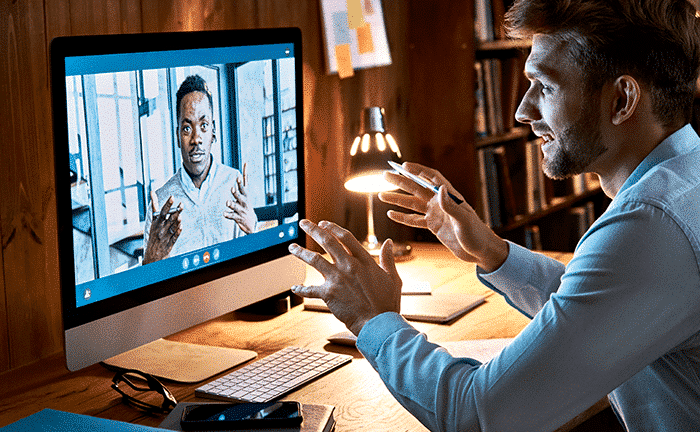
Create better experiences for candidates, hiring managers and HR teams
In today’s new world of work, finding and keeping the top talent requires a holistic strategy for managing the talent acquisition process. Our team works with you—from understanding your culture and employment branding to providing assessments and hiring decision support tools—to help you find and keep the best talent.
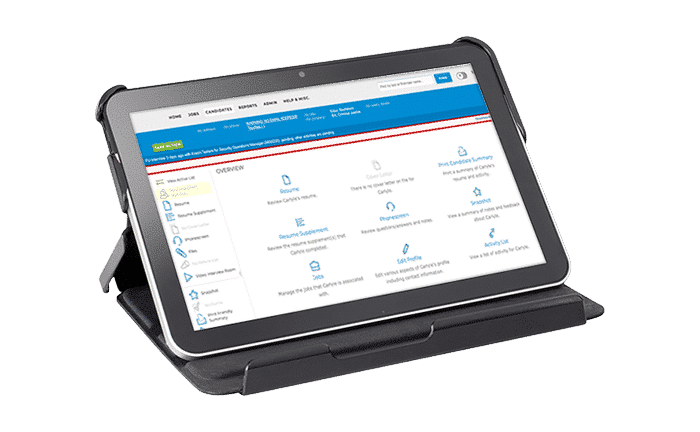
Hi-tech solutions for a best-in-class experience
Our plug-and-play technology stack adapts to your requirements and hiring systems. Offering transparent insight into each step of the recruiting process, we can offer a full-service ATS or integrate with your internal systems to function as a seamless extension of your team.
97% of our clients say we’re their first choice

SUCCESS STORY
Delivering exceptional results
Learn how Engage2Excel Recruitment Solutions helped Dickinson Fleet Services overcome unprecedented talent shortages to deliver 463 new mobile tech employees. Our high-touch talent acquisition strategy gets candidates’ attention, keeps them engaged through the process and lets them know that they are valued.